Chapter 12: The Murder Mystery Method
This chapter is adapted from [ 12 ].
We describe here a variation of the usual procedure for determining whether a vector field is conservative and, if it is, for finding a potential function. We have used this method, which we call the murder mystery method, in our own classes for many years; students love it.
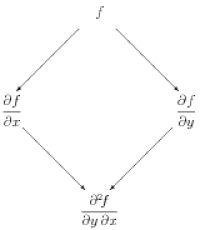
It is helpful to make a diagram of the structure underlying potential functions and conservative vector fields. For functions of two variables, this is shown in Figure 12.1a. The potential function $f$ is shown at the top. Slanted lines represent derivatives of $f$; derivatives with respect to $x$ go to the left, while derivatives with respect to $y$ go to the right. The second line thus gives the components of $\grad f$. The bottom line shows the mixed second derivatives, which can of course be taken in either order.
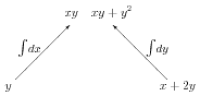
But we are not given $f$. Rather, we are given a vector field, such as \begin{equation} \FF = y\ii + (x+2y)\,\jj \label{2dexample} \end{equation} and need to determine whether it is conservative, that is, whether $\FF$ is the gradient of some potential function $f$. This is the second line of the diagram! We could start by checking the mixed derivatives. However, what we really want is the potential function; we should be moving up the diagram, not down. What happens if we simply integrate both components, as shown in Figure 12.2a? The potential function is clearly contained in the results of these two integrals; it is just a question of combining them correctly.
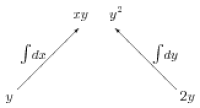
Furthermore, there is enough information here to determine whether $\FF$ is conservative in the first place; there is no need to check the derivatives. For example, had we been given the vector field \begin{equation} \HH = y\,\ii + 2y\,\jj \end{equation} and attempted the same procedure, we would obtain Figure 12.2b. Simply by noticing that $xy$, a function of two variables, only occurs once, we see that $\HH$ is not conservative.
We describe this to students as a murder mystery. A crime has been committed by the unknown murderer $f$; your job is to find the identity of $f$ by interviewing the witnesses. Who are the witnesses? The components of the vector field. What do they tell you? Well, you have to integrate (“interrogate”) them! Now for the fun part.
If two witnesses say they saw someone with red hair, that doesn't mean the suspect has two red hairs! So if you get the same clue more than once, you only count it once.
On the other hand, some clues require corroboration. These witnesses were situated in such a way that each could only look in one direction. Thus, one witness, the $x$-component, only sees terms involving $x$, etc. If a clue contains more than one variable, it should have been seen by more than one witness! In fact, functions of $n$ variables should occur precisely $n$ times. In the case of the vector field $\HH$, the clue $xy$ was only seen by one witness, not both; somebody is lying! In short, clues must be consistent.
Here is the Murder Mystery Method in a nutshell:
- Integrate: Integrate the $x$-component with respect to $x$, etc.
- Check consistency: Functions of $n$ variables must occur exactly $n$ times.
(If the consistency check fails, the vector field is not conservative.) 1) - Combine clues: Use each clue once to determine the potential function.
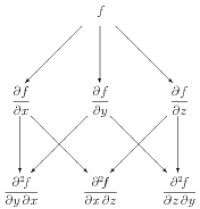
The power of the murder mystery method is even more apparent in three dimensions. We encourage the reader to try to find a potential function for the vector field $\GG$ defined by \begin{equation} \GG = yz\,\ii + (xz+z)\,\jj + (xy+y+2z)\,\kk \label{3dexample} \end{equation} using this method. The underlying structure is shown in Figure 12.1b, where now $y$ derivatives are shown going straight down, and $z$ derivatives go to the right.
Consistency is traditionally checked by computing the last line of the appropriate diagram in Figure 12.1. We reiterate that this is not necessary with the Murder Mystery Method. This computation can be introduced afterward to motivate the algebraic formula for curl in rectangular coordinates. (We save the geometric definition until after we have covered Stokes' Theorem.)
Finally, this method also generalizes to bases adapted to other coordinate systems, such as polar coordinates — especially since the “differentiation” step, namely the calculation of the curl, is omitted. For example, the natural polar basis consists of $\rhat$, the unit vector in the radial direction, and $\phat$, the unit vector tangent to circles $r=\hbox{constant}$. Recalling from (14) in §4.2 in Chapter 4 that \begin{eqnarray*} \grad f = \Partial{f}{r}\,\rhat + \frac{1}{r}\Partial{f}{\phi}\,\phat \end{eqnarray*} leads quickly to a version of the Murder Mystery Method in polar coordinates; the only real change is the need to include a factor of $r$ before integrating with respect to $\phi$. The procedure is similar in cylindrical or spherical coordinates.